Linux has a robust file permission system to maintain the system’s security. You can manage these permissions properly to safeguard your system from unauthorized access and security breaches. The root user can use all these file persimmon (read, write, or execute) and assign it to other users. However, many users don’t know about Linux file permissions, its fundamentals, various permission categories, etc.
This lack of knowledge can result in unauthorized access and issues with the executable files. So, this blog has in-depth information to help you understand the Linux file permissions to secure the system.
Contents
Understanding the Linux File Permissions: How to Secure Your System
Let’s divide this section into multiple parts to explain the basic and advanced explanations of Linux file permissions.
1. Basics of File Permissions in Linux
Linux features the “chmod” command to set these file permissions. Its syntax is:
chmod [owner], [group], [other users] [filename]
- Owner (u): This represents the user who owns the file or directory. The owner has the most control over a file, and they are the only ones, apart from the root user, who can change that file’s permissions.
- Group (g): The specified file can be owned by a group of users, and the group permissions apply to all its members. This kind of ownership is helpful when working on collaborative projects.
- Other users (o): It represents the level of access for all the other users like the general public.
The permissions are of the following types:
- Read (r or 4): The “read” permission allows the users for a view-only access to the file which means that they can view and list the content of the directory or file. The users can only access a file once they have the “read” permission.
- Write (w or 2): With this permission, the users can modify the contents of a file or create, delete, and rename the other files within a directory.
- Execute (x or 1): The “execute” permission is essential for the executable files such as programs and scripts. Users can only run a program if they have the “execute” permission.
Furthermore, the user category and the permissions are connected by a “+” or “-‘” sign in the command. The “+” sign tells the system to give the mentioned permissions, whereas the “-“ sign is to remove them.
If you want to give all permissions to the owner, the “read” and “write” permissions to the group, and the “read-only” access to others, you can use the following command:
chmod u=rw,g=r,o=r <path of the directory>
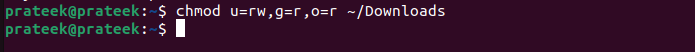
In the previous commands:
- The u=rw is for the “read” and “write” permissions for the owner.
- The g=r is for the “read” permission for the group.
- The o=r is for the “read-only” permission for others.
You can use the following command to check the assigned file permissions:
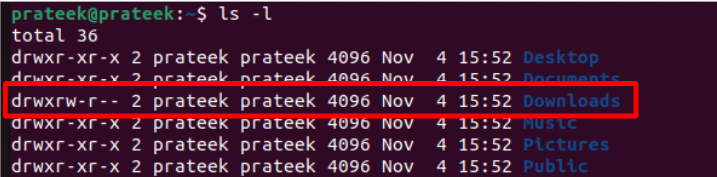
Moreover, if a file or directory has already given extra permissions to the users and you wonder how to take that access back, you can use the “-“ sign and mention what permission to remove.
2. The Octal Notations in Linux File Permissions
The previously mentioned format demonstrates the command using symbolic notations. If you want to use the octal notations instead, use the following command:
Replace “u”, “g”, and “o” with the octal value of permissions that you want to grant the owner, group, and others. The octal values are calculated as follows:
- The “read”, “write”, and “execute” permissions have their separate values of 4, 2, and 1, respectively. To get the octal value of two or three permissions combined, add their unique values.
- The rwx(read, write, and execute) permission has an octal value of 4+2+1= 7.
- The rw(read and write) permission has an octal value of 4+2= 6, and so on.
chmod 764 <path of the directory>
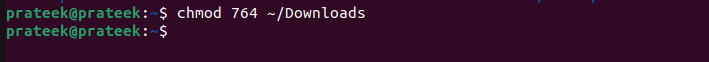
In the previous command:
- 7 is for the owner (4 for read, 2 for write, 1 for execute)
- 6 is for the group (4 for read, 2 for write)
- 4 is for others (4 for read)
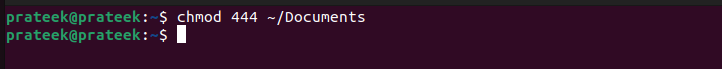
For instance, let’s grant the “read-only” access to all user categories:
How to Use the Linux File Permissions for System Security
After understanding the Linux file permission concept, it is essential to follow some practices that ensure a maximum system security.
- File Permission Essentials: Always ensure that only the necessary users have the required permissions, and try to keep the executable permission to admins only. Properly assigning these permissions can help you prevent malicious and potentially unwanted programs from damaging your system.
- Utilize File Encryption: It’s best to encrypt the confidential files and programs. This way, you can protect your sensitive data. Tools like GNU Privacy Guard facilitate the encryption methods that you can use to shield your data from prying eyes.
- Using Advanced File Permissions: You can further use permissions like setuid, setgid, and sticky bits to allow the permissions only to specific users. You can use them to avoid granting an access to unwanted users.
- Implement Role-Based Access Control (RBAC): Always follow the principle of the least privilege and use RBAC to assign permissions based on a user’s role and responsibilities. These are the fundamental concepts to maintain the system security.
Conclusion
Understanding the Linux file permissions is essential to secure your system from unauthorized access. We included all the best practices that you can use to secure your Linux system. These practices included file encryption, role-based access, and essential file permissions. You should always provide an executable access to the system administrators only. Furthermore, don’t provide the executable permissions to any random file. Otherwise, it may sometimes create errors.
