Centralized Storage: The database provides a centralized location to store all your findings, making it easier to access and manage your penetration test data.
Efficient Collaboration: When working in a team, the database enables a seamless collaboration by allowing multiple users to access and update the same information.
Historical Tracking: With the database, you can track the changes over time, enabling you to analyze how vulnerabilities have evolved and been addressed.
Contents
Setting Up the Metasploit Database
Start PostgreSQL Service
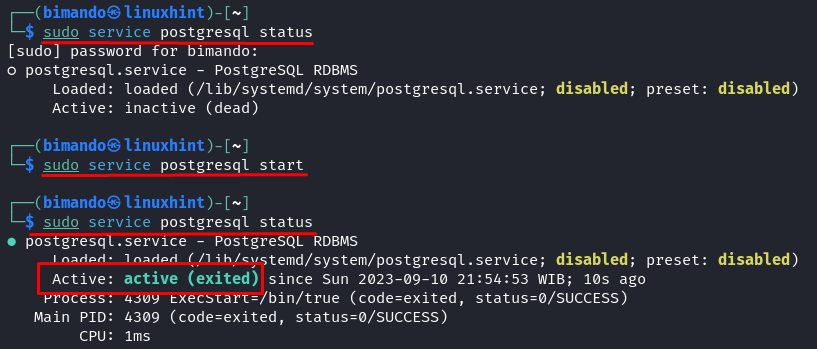
The Metasploit database operates using a PostgreSQL server. By default, this server doesn’t start automatically. Therefore, ensure that you initiated the service using the subsequent command:
sudo service postgresql start
Initialize the Database
Open Metasploit and initialize the database by running the “msfdb init” command. This command creates the necessary database structure.
Start the Database Service
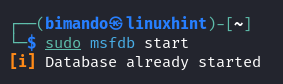
Ensure that the Metasploit database service is running by executing “sudo msfdb start”.
Test the Configuration
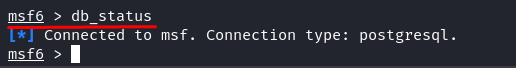
To confirm that everything is working as expected, run the “msfconsole” and check if the database is connected using the “db_status” command.
Creating and Deleting a Workspace
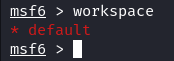
Before we jump into any exploitation, we should set an appropriate workspace. The workspace is a place to organize our environment and exploitation. Type the “workspace” command from the msfconsole. It displays the currently selected workspaces. The database automatically opts for the “default” workspace when you establish a connection, indicated by the asterisk (*) next to its name.
Let’s first analyze what are the available arguments to handle this workspace by typing the following:
| Argument | Detail |
| -a, –add <name> | Add a workspace |
| -d, –delete <name> | Delete a workspace |
| -D, –delete-all | Delete all workspaces |
| -h, –help | Help banner |
| -l, –list | List the workspaces |
| -r, –rename <old> <new> | Rename a workspace |
| -S, –search <name> | Search for a workspace |
| -v, –list-verbose | List the workspaces verbosely |
Based on the given help info, to create a workspace, simply use the “-a” followed by the workspace name as follows:
msf6> workspace -a bimando_db
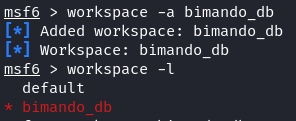
After generating a new workspace, the previously set default workspace is replaced with the newly created one. To transition between workspaces, you can easily reference the workspace name as demonstrated in the following:
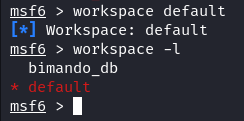
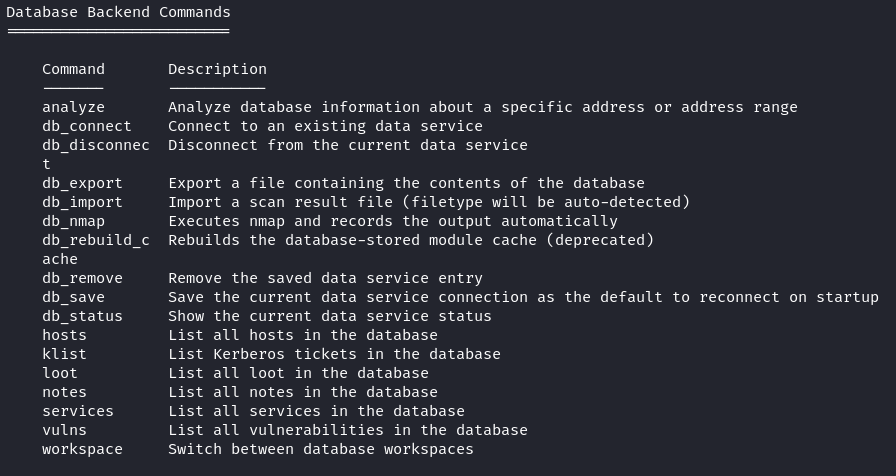
Now that your database is prepared, you can move forward with your penetration test. Metasploit autonomously records the information, enabling you to examine the outcomes by running queries on the database. You can access a detailed compilation of database commands using the “help” command which is conveniently located in the “Database Backend Commands” section.
Conclusion
In summary, integrating the Metasploit database offers substantial benefits for organizing the penetration test activities and findings. It streamlines the storage and retrieval of vital information concerning vulnerabilities, exploits, and hosts, resulting in a more organized and efficient process. Additionally, the Metasploit database provides advantages like centralized data storage, facilitating easier access and management, promoting seamless teamwork, and enabling historical tracking of developments over time.
Incorporating the Metasploit database into your arsenal for penetration testing not only streamlines your workflow but also fosters collaboration and provides valuable insights for your security assessments.
